Introduction of Network Security and Firewalls
Network security and firewalls play an important role in protecting. And ensuring networks to keep connected devices connected to each other in the world. Be it personal computers or business systems or any industry or factory or government infrastructure. And rely on and for the transfer of their data and secure all data. And protect it from cyber-attacks in which such No firewall plays an important role.
Network security refers to the process of creating policies in a new way. And then creating a platform to protect the network. And its data from non-virtual access, abuse, and misuse through technologies that protect all data. Protect and ensure the integrity of information, confidentiality. And data that is stored, and control all traffic that flows through it. And between trusted internal networks and untrusted external networks such as the Internet. Act as a barrier.
Principal Branches of Network Security and Firewalls
Network Security is a broad platform that spans several key areas with a unique focus and technique. Cyber security is a complex field, but it can be managed with a few principles to ensure privacy and security. A limit controls the traffic to and from the design of all authentication work.
- Access Control
An access network ensures that users can access their devices on the network by protecting their documents and personal data from hackers, such as users’ names and passwords or biometric authentication, and protecting users’ data keys. Yes, it involves primarily identifying security tools.
- Network Monitoring and Intrusion Detection
Networking monitoring and intrusion detection are two important branches of networking security.
Networking involves continuously identifying and monitoring networking activity to detect suspected hackers and respond in a new way. While the IPS takes key steps to prevent and protect against intrusion prevention systems. Managed Detection and Response (MDR) encryption.
- Data Encryption
Coding and protecting data in a secret manner so that users can understand it or ensuring confidentiality of data during transmission is called data encryption. And any trading system requires security measures to encrypt and conform to its standard trading practices.
- Endpoint Security
Endpoint security focuses on protecting and protecting individual situations such as laptops, smartphones, tablets from cyber attacks, including antivirus software, development management tools, and page updates. Protects infrastructure components such as network services and data centers Uses multi-factor authentication MFA to provide an additional layer of security for username and password entry.
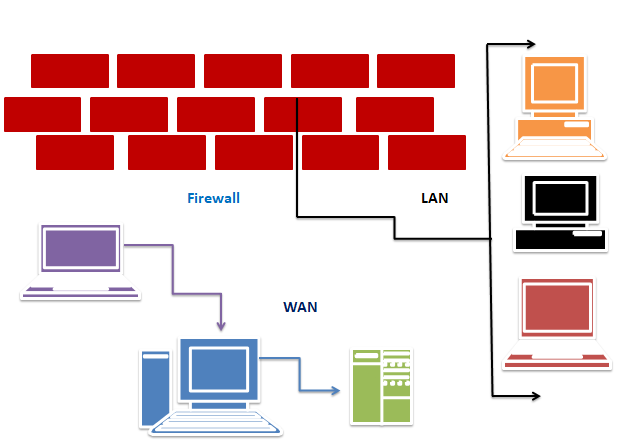
- Firewalls
Firewalls act as gatekeepers of networks in that they block non-virtual cyber attacks while allowing legitimate traffic and can be hardware-based, software-based or cloud-based. The firewall looks at things like iPod races, domain names, and protocols to decide whether an update packet is worthy of entering the network.
Virtual Private Networks (VPNs)
There are main types of virtual private networks.
A VPN creates a secure unencrypted connection over the Internet, ensuring that data transmitted between devices will not be exposed and protected. The use data program uses the UDP transport lens for interaction and creates a new version and new software to use in PPTP.
- Application Security
Application security this includes protecting the application from vulnerabilities and threats during development and deployment, such as software that no coder can open in an unauthorized manner, and vulnerability screening and penetration testing. Protects entire network infrastructure including ware and security protocols Network Security and Firewalls tools include Fiber Walls VP anti-malware software and intrusion prevention systems that protect individual applications from cyber-attacks, access and malicious access Protects against cyber attacks based on.
- Cloud Security
Cloud Network Enhances Security Services and Enhances User Experience Cloud Security ensures the security of process data stored on any website and controls all processes on the network communication and configuration. A key focus of securing is the network partitioning namespace; the overlay addresses network traffic filtering and encryption aspects.
Sub-Branches of Network Security
Each of the principal branches focuses on specific aspects of Network Security and Firewalls protection and further sub-branches which are as follows.
- Access Control Sub-Branches
Role-based access control allows RBAC to restrict access to resources to specific users based on user roles Network (VPNSA) distributed function in a LAN groups devices according to development or security levels, with the administrator providing a new protocol to the network. Does and plays an important role in denying permission to traffic on it.
- Permits based on the role of the user i.e. the user are not selecting the data for any misuse.
- Permissions depend on specific pages, such as time or location, and control over them increases as they are used.
- Data Encryption Sub-Branches
Uses a master key and key for encryption and decryption and securely uploads any data it contains to the website.
- Firewall Sub-Branches
Packet Filtering Firewalls
- Four minutes go through the data packets and allow them to block or open based on the rule.
- Protects interactions between users and their underlying decisions.
- Cloud Security Sub-Branches
Identity and Access Management (IAM)
In the cloud, it waits for users’ permission and waits for clicks to react.
Conclusion
Firewalls play an important role in digital security, protect against cyber threats, play an important role in Network Security and Firewalls , and work together to create a well-defined system such as understanding them. helps to create better security measures and ensures that their data critical systems are protected from malicious elements and no hacker can steal or disrupt any website. It can and will be a huge challenge A firewall is built to prevent them.
360WebSol